"batman"
So, sometimes the Internet is just… well… weird.
And I suppose, sometimes, I am too…
The other day, I was just sitting and watching the packets hitting one of my honeypot systems stream by.
I find it soothing.
Suddenly, out of the corner of my eye, I noticed something odd fly by.
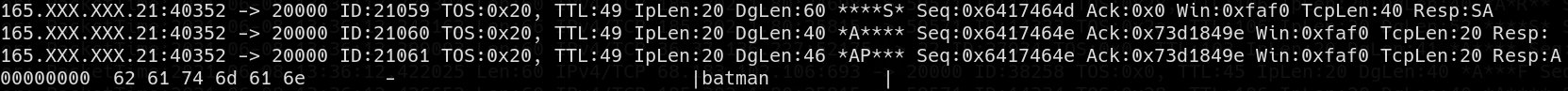
No… That didn’t actually say…!?!?
I scrolled back up and yes, indeed, I did see what I thought I saw:
 (click to enlarge)
(click to enlarge)
I can generally figure out what the heck is going on with teh packetz.
Not this time…
I’m stumped.
(There is some sort of routing protocol for ad-hoc mobile mesh networks that goes by the name Batman, but I don’t think that this is related to that.)
While I don’t have a clue what this is actually about, I do know this: They messed it up. Big time.
I’m really a nice guy (just ask me, I’ll tell you…). I’m all about fixin’ stuff that other people mess up. So, while I don’t know what sent that packet - or why - I’ve taken it upon myself to fix it. I give you, batman.py, a little Python script that does it right:
#!/usr/bin/env python
import socket as s
import time as t
p = 12345
def send(m):
S = s.socket(s.AF_INET, s.SOCK_STREAM)
S.connect(('127.0.0.1', p))
S.sendall(m)
S.close()
for i in range(16):
send(b'na\n')
t.sleep(0.5)
t.sleep(1.5)
send(b'batman\n')
The original Python script was designed to fit into a tweet. If you want to be a ‘Netmenace, you can (obviously) change the IP address and port number and confuse the heck out of your target which must (again, obviously) accept inbound TCP connections on whatever port you choose.
Alternatively, if you want to see it in action locally, you could just run:
socat - TCP-LISTEN:12345,fork,reuseaddr
(Note: If you’re really lazy, here’s a pcap file.)
There… I fixed it.
-TL
Tom Liston
Owner, Principal Consultant
Bad Wolf Security, LLC
Mastodon: @tliston@infosec.exchange
Twitter: @tliston
May 10, 2021